The Open-Source
Headquarters for AI Agents
Lattice is where AI agents get their identity, their permissions, their compute, and their orders. From a weekend hack to Fortune 500 governance — self-hosted, vendor-neutral, runs anywhere.
brew install latticehq/lattice/latticeEnterprise Trust Requires Scale
Historically, meeting enterprise security requirements has required large organizations with dedicated platform teams.
Application-Level Enforcement
Every AI company re-implements SSO, RBAC, audit logs, and compliance controls inside their application code.
- ✗Expensive engineering resources
- ✗Diverts from core product development
- ✗Trust depends on code discipline
Coupled to Team Size
Enterprise readiness becomes tightly coupled to organizational scale and team maturity.
- ✗Small teams can't compete
- ✗Innovation slowed by infrastructure work
- ✗Enterprise deals require large teams
The result: Only large organizations can ship software that enterprises trust.
This creates an artificial barrier between individual innovation and enterprise deployment.
Move Enforcement Into the Runtime
Lattice decouples trust from team size by providing a complete headquarters — enforcement, compute, operations, and community — as open-source infrastructure.
Declare Constraints
Agent developers declare identity, authorization, audit, and deployment constraints once.
Runtime Enforcement
Lattice sits in the execution path and enforces constraints before actions are executed.
Violations Blocked
Policy violations are structurally impossible — enforcement happens by design, not by discipline.
For Enterprises
- Enforced by RuntimeTrust is structural, not based on vendor promises
- Auditable & ProvableAll enforcement decisions are transparent and inspectable
- Deploy AnywhereCloud, self-hosted, or air-gapped environments
For Developers
- Build Capabilities, Not InfrastructureFocus on agents, not enforcement systems
- Enterprise-Ready from Day OneShip to enterprises without a platform team
- Zero API CostsLocal inference on your hardware, no monthly bill
From solo hacker to Fortune 500 — same platform, same codebase, same community.
Your agents. Your models. Your rules. Your infrastructure.
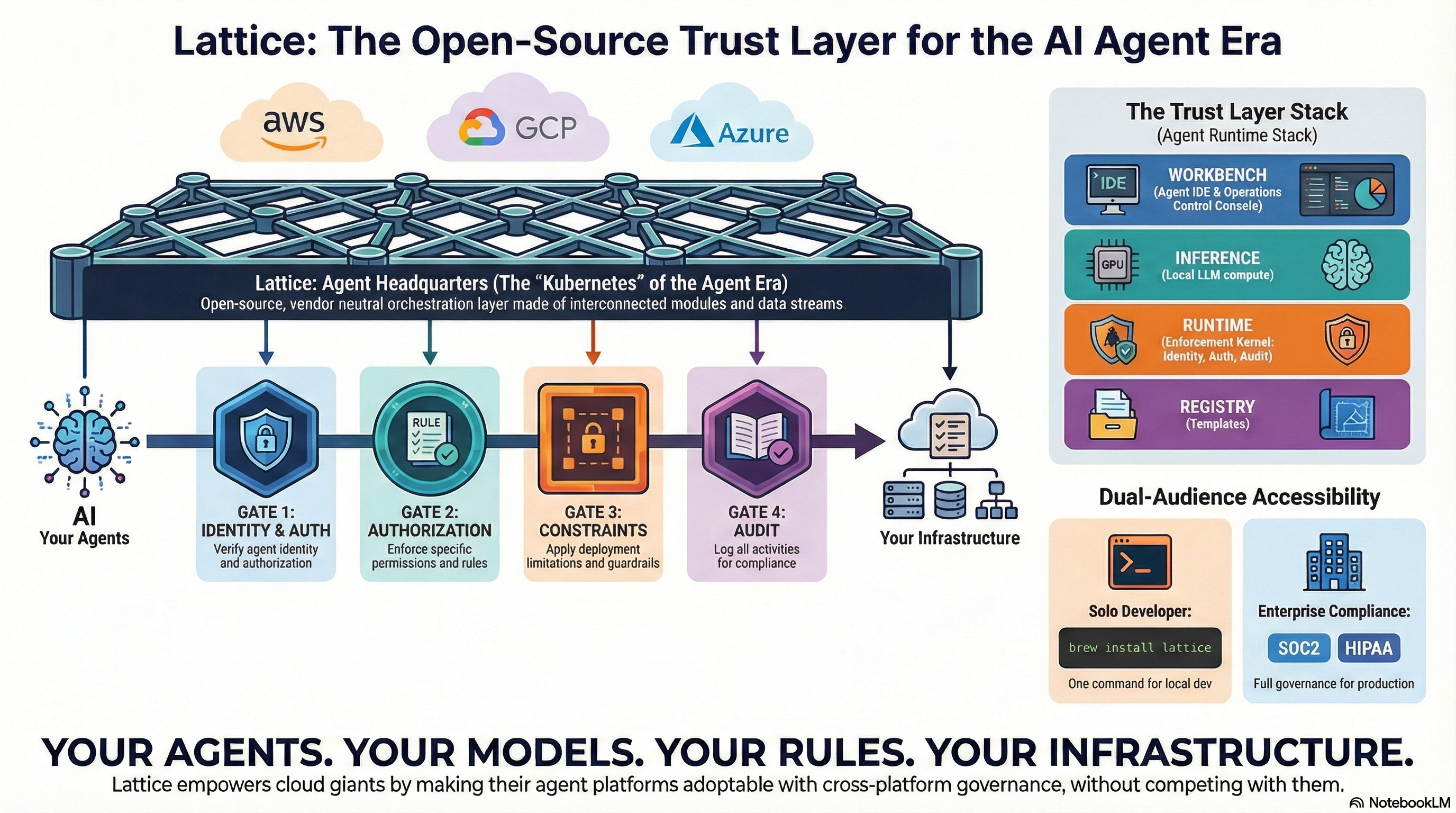
Agent Headquarters
Five integrated components. One open-source platform. Everything your agents need.
Runtime
The Kernel
Enforcement engine — identity, authorization, audit, deployment constraints. Every agent action passes through four gates.
Inference
The Compute
Local LLM serving on your hardware. MLX for Apple Silicon, CUDA for NVIDIA. mDNS autodiscovery forms GPU clusters automatically.
Workbench
The Interface
Agent IDE and operations console. Multi-model chat, real-time monitoring, cost tracking. Desktop, web, CLI, VS Code.
Registry
The Ecosystem
Community templates, modules, and presets for Docker, Kubernetes, AWS, GCP, Azure. Deploy agents anywhere in minutes.
Enterprise
The Scale Layer
Admin control planes, policy lifecycle, directory integration (AD, Okta, LDAP), compliance exports (SOC2, HIPAA, FedRAMP).
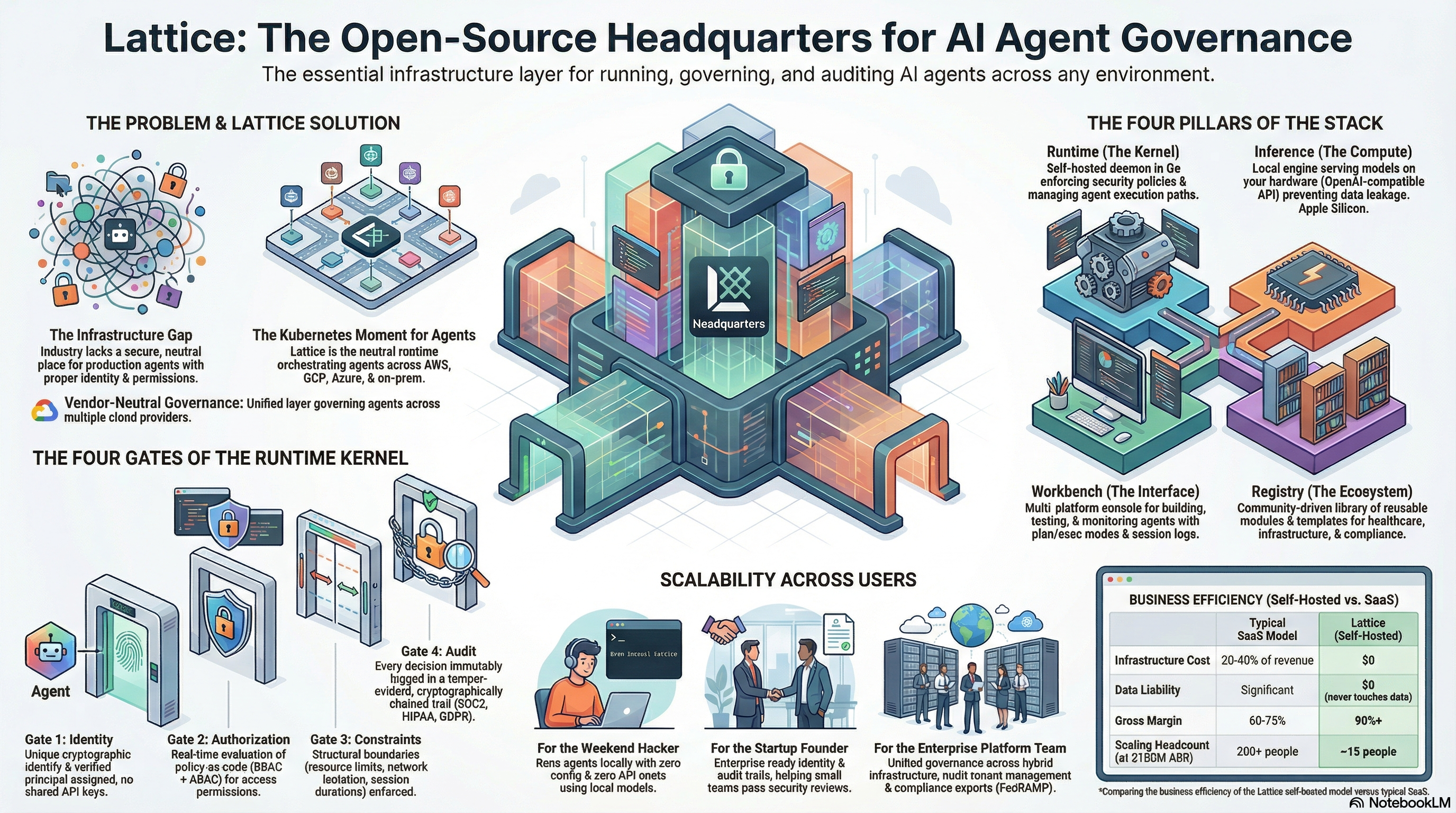
What Lattice Enforces
Four core enforcement layers that operate in the execution path, making violations impossible by construction.
Identity
Who or what is making the request?
Cryptographically verified identity for every agent, user, and service across cloud, self-hosted, and air-gapped environments.
- »OAuth 2.0, OIDC, SAML, mutual TLS, API keys
- »Unique cryptographic principal per agent
- »Cross-environment identity federation
- »Zero-trust identity model
Authorization
Is this action allowed?
Policy-as-code evaluated at runtime, not coded into applications. Fine-grained control over what agents can do.
- »RBAC + attribute-based policies (ABAC)
- »Fine-grained resource permissions
- »Dynamic real-time policy evaluation
- »Cross-platform consistency
Audit
What happened and when?
Immutable, tamper-evident records of every enforcement decision and agent action for compliance and forensics.
- »Cryptographically chained audit trail
- »Compliance reporting (SOC2, HIPAA, FedRAMP, GDPR)
- »Queryable event history
- »Real-time event streaming
Deployment Constraints
Where can this run?
Structural boundaries on agent execution — where they can run, what resources they consume, and when.
- »Environment and geographic restrictions
- »Network segmentation enforcement
- »Resource quota management
- »Air-gap validation
Your Models. Your Hardware. Zero API Costs.
Run LLMs on your own machines with an OpenAI-compatible API. Data never leaves your infrastructure.
The Governance Layer Every Cloud Needs
Unified governance across every agent platform, every cloud, every environment. Vendor-neutral by design.
Multi-Cloud Enterprises
Bank deploying across GCP + on-prem? Hospital spanning multiple systems? Lattice provides unified identity, auth, and audit across every environment.
Air-Gapped Deployments
Defense, healthcare, government — Lattice runs fully offline with zero internet access. Complete governance in disconnected environments.
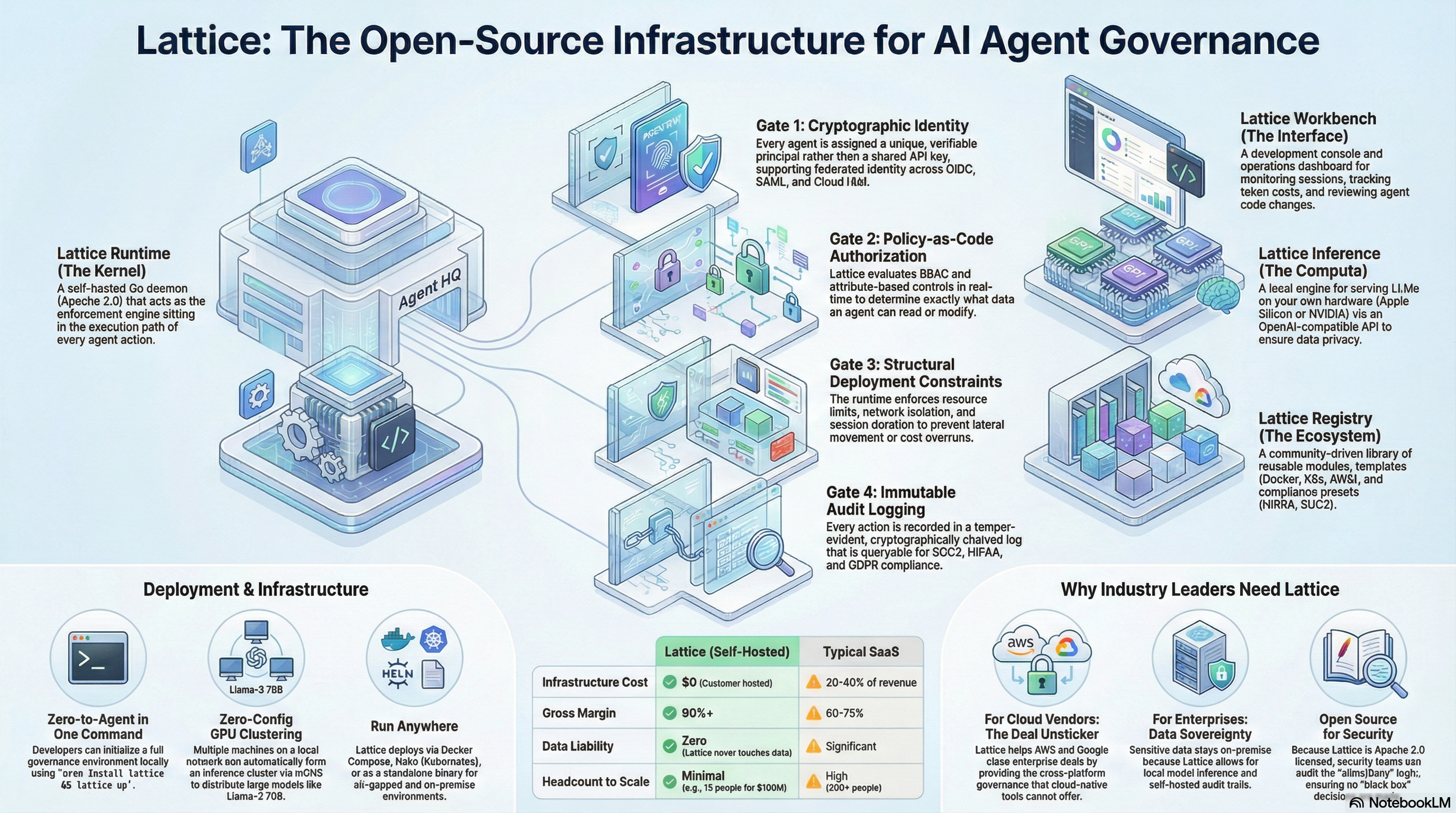
How Lattice Works
Five components working together — from enforcement kernel to developer interface.
Open Source (Apache 2.0 / MIT)
Runtime, Inference, Workbench, and Registry are fully open source and auditable.
- ✓Identity and authorization evaluation
- ✓Policy decision engine
- ✓Audit event generation
- ✓Local LLM inference serving
- ✓Agent IDE and operations console
Why open? Enforcement must be auditable. If the software decides "allow" or "deny," you can read the code.
Commercial (Enterprise Edition)
Enterprise governance, administration, and compliance features for organizations at scale.
- ✓Administrative control planes
- ✓Policy lifecycle management
- ✓Directory integrations (AD, Okta, LDAP, SAML)
- ✓Compliance exports (SOC2, HIPAA, FedRAMP)
- ✓Multi-tenant organizational governance
Why commercial? These components don't decide "allow vs deny" — they standardize operation at scale.
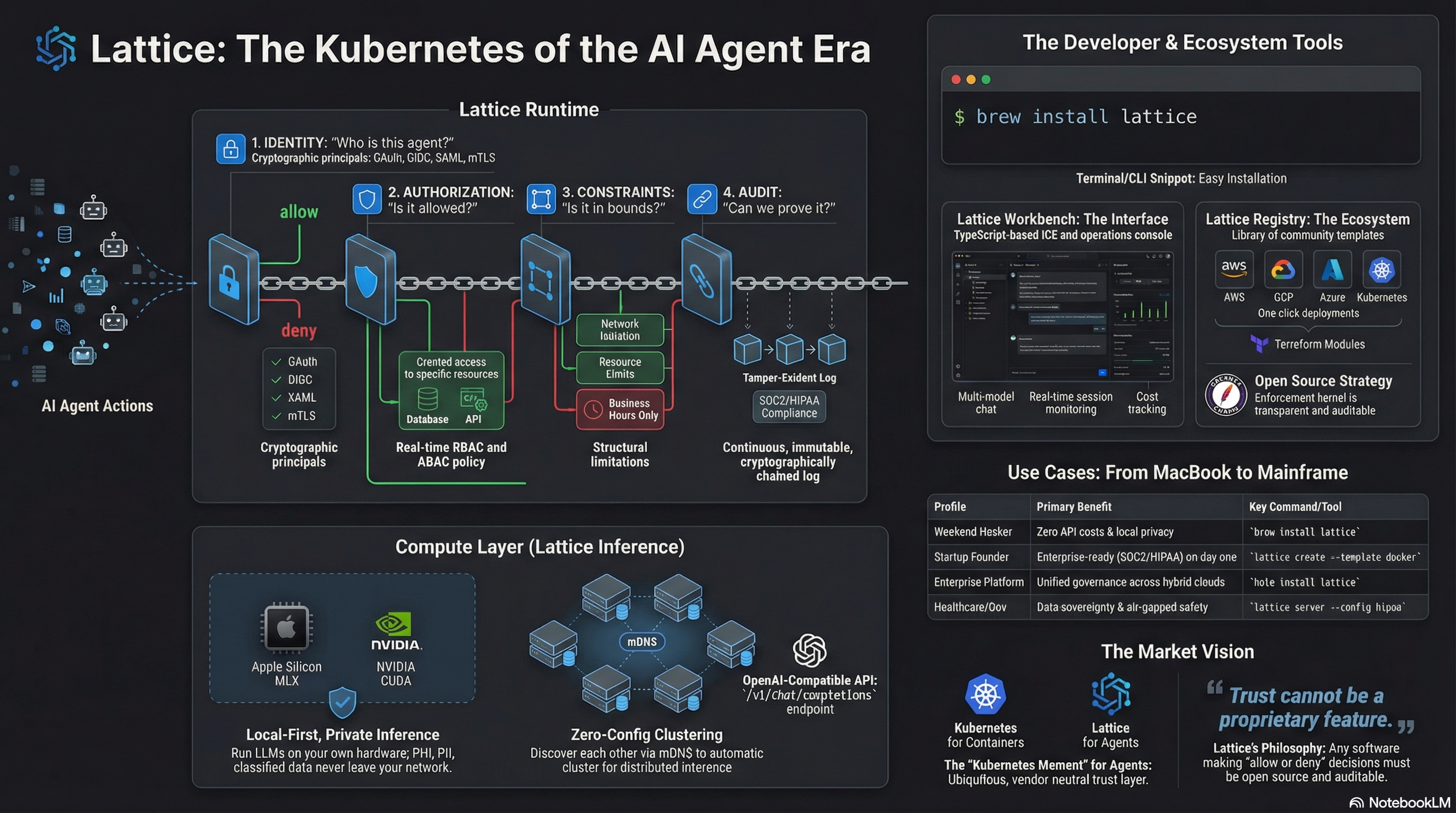
Up and Running in Three Commands
Install Lattice, start your headquarters, deploy your first agent.
Same Platform. Every Scale.
From a weekend hack to Fortune 500 production — Lattice grows with you.
Weekend Hackers
brew install and go. Free local inference, no API bill, no credit card. Your agents run on your machine with full governance.
Startup Founders
Enterprise-grade governance from day one. Ship to enterprises without hiring a platform team. SOC2 and HIPAA compliance built in.
Enterprise Platform Teams
Unified governance across every cloud, every system. Self-hosted, auditable, vendor-neutral. Integrates with AD, Okta, LDAP.
enterprise@latticeruntime.comJoin the Community
Lattice is in active development across five open-source repositories. We welcome contributions, feedback, and early adopters.
GitHub
View the ecosystem, report issues, contribute code
hello@latticeruntime.com
Security
Report vulnerabilities
Interested in Enterprise Edition?
We're working with select early partners to shape the enterprise features. Get in touch to learn more.
CONTACT ENTERPRISE TEAM